A software escrow agreement involves three parties: the software manufacturer, the software user and its digital enterprise resource planning (ERP) system, and last but not least, the escrow agent, acting as a neutral intermediary. How does it work, and what are the biggest mistakes you can think of?
Seven myths of software escrow
MYTH no. 01
SECURE, REGULAR SOFTWARE STORAGE IS POINTLESS AND UNNECESSARY.
Let’s try to think about it. Imagine a person who believes that their house will never be robbed, that they will never have a car accident or that they will not need medical treatment. If any such thing happens, there is a big difference in whether or not she has adequate insurance to help her. The same principle applies to technology storage, and so it’s insurance: we hope we never need it, but I want to make sure that it’s here when I need it – and it works.
We have entered into a partnership with butteland s.r.o. to ask software quality and software testing experts about the risks of licensing critical technologies. More than half of their clients said they had entered into a relationship with a vendor to use mission-critical applications for their business that did not meet their expectations. The standard reason for this failure was a repeated breach of Service Level Agreements (SLAs), which can be easily remedied. However, 35% mentioned reasons that are more difficult to bounce off: application support terminated, merger or acquisition, or bankruptcy or insolvency of the seller. These are the most common reasons we have encountered in even greater numbers since the start of the COVID-19 pandemic. These reasons clearly demonstrate the importance and reason why software storage is necessary.
MYTH no. 02
IT IS LIKELY THAT THE SECURED SOURCE CODE WILL BE INCOMPLETE OR OUT OF DATE.
We strongly recommend a specific level of custody verification for each custody agreement. Here, we ensure that if the source code is released from storage, it will contain everything necessary, including the functional specifications needed to efficiently read, recreate, and maintain your own in-house technology — or seamlessly transition to another vendor. We can use a simple comparison to physically inspect a professional athlete to make sure he is in good health before signing a contract.
In addition, in order to ensure that your software is current, it is necessary to specify, in the Software Escrow Agreement, the frequency of updates and the regular recording of releases from your software vendor.
MYTH no. 03
EVEN IF WE GET THE FULL SOURCE CODE FROM THE VAULT, WHAT DOES IT HELP, WHEN WE HAVE NO EXPERIENCE USING IT?
You have several options to choose from. These include self-maintaining your software or application – or hiring someone to do it for you. Interestingly, more than half of the companies we spoke to about their recent releases have hired former programmers from their defunct software vendor to maintain the product. After all, it makes sense to keep software/applications that are vital to the client in-house. Especially if their dysfunction directly affects their annual turnover.
MYTH no. 04
THE RELEASE OF THE SOURCE CODE IS ACCOMPANIED BY DELAYS AND LEGAL ACTION.
On the contrary, the main advantage of releasing source code from custody is the ability to avoid costs and delays in bankruptcy proceedings against the administrator, other creditors or anyone who claims to be a licensee and you do not have the right to the source code. The vast majority of custody releases go smoothly without the need for litigation. In two decades, the number of arbitration disputes with the judicial agreement is 0.688%.
Escrow simplify things.
MYTH no.05
SOFTWARE ESCROW SERVICES ARE TOO EXPENSIVE.
In fact, concluding a software custody agreement is not expensive at all. You can contact butteland to see the sample contract and the price list of Software Escrow services.
MYTH no. 06
WHEN PEOPLE SWITCH TO SAAS, SOURCE CODE STORAGE IS UNNECESSARY.
Today, many companies rely on software as a service or software as a live service for its critical business processes. It makes sense to assume that software storage is no longer needed. But, it’s a false belief – if the software vendor declares a crash for some reason, regardless of whether its applications were running on the cloud and you used them this way, it will no longer be possible. Even the largest cloud providers will not guarantee business continuity, and you will also not get to the source code. The only software escrow service on secure TIER 4 server spaces in our TÜV SÜD company will provide you with the source code in the event of a similar disaster. It is also important to add that your SaaS provider’s business continuity/disaster recovery does not apply to your application and data.
That’s the reason why TÜV SÜD has developed its “SaaS coverage” solutions for business continuity. These services offer disaster recovery and risk management solutions for both SaaS providers and subscribed customers.
MYTH no. 07
IT DOESN’T MATTER WHICH ESCROW VENDOR YOU CHOOSE, IT’S A COMMODITY TRADE.
As with most things in life, you have to trust who you do business with. TÜV SÜD is a renowned global provider of professional solutions in the field of quality and safety.
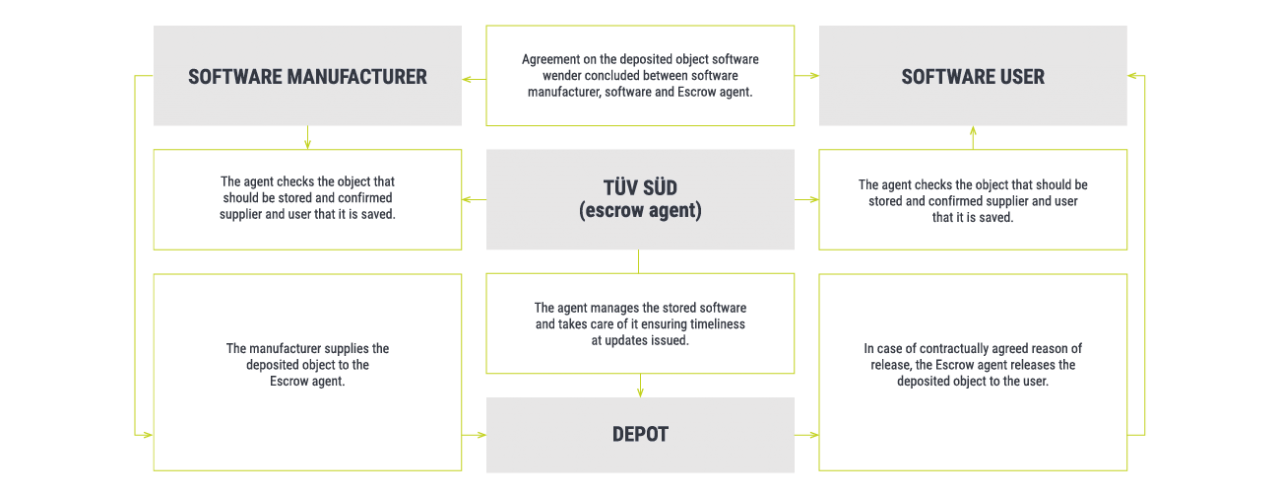
What is the importance of escrow procedures?
Software escrow procedures offer benefits for both contractual parties: Software users assured that the source code is securely deposited. Software manufacturers using the services for reliable intellectual property documentation, thereby offering their customers clear security advantages.
SAR testing capabilities
Software Escrow Services comprise a bundle of highly complex activities which extend from incoming tests for completeness and freedom from viruses and malware to special bespoke tests according to individual requirements. To maintain the fault-free condition of the software in updates and further releases, technical documentation and release notes to the escrow agent also form part of the agreement.
- Software incoming test
- Source code verification
- Software quality assurance (e.g. testing the functionality, ergonomics and data security of software systems and consulting on requirements)
- Updating of the saved source code
- Optional possibilities such as software walkthroughs and test compilations
- Project-specific escrow services, special models


